How do you know a download wasn’t corrupted, a software update wasn’t swapped, or a cloud machine is really running the code you trust? The answer is verification – methods that prove data and software are authentic and unchanged. We’ll start with everyday tools like file checksums and then move to Trusted Execution Environments (TEEs), a hardware-backed “safe room” for sensitive code and data. Along the way, you’ll see how remote attestation lets you trust a computer you don’t control, and how developers link open source code to what actually runs. We’ll use simple metaphors – sealed packages and verified couriers—to make each step clear.
Why Verification Matters
Everyday metaphor: a sealed package.
When a parcel arrives, you check two things: the tamper-evident seal and the tracking number. If the seal is intact and the tracking number matches the seller’s record, you trust the contents. In computing, verification plays the same role: it tells you whether data or code has stayed the same from sender to receiver.

Hashes: Digital Fingerprints for Integrity
A cryptographic hash function takes any input (a file, message, or program) and produces a fixed-length output called a hash or checksum. Treat it like the package’s tracking number or a digital fingerprint.
Good cryptographic hashes have four key properties:
-
Deterministic: The same input always gives the same hash.
-
One-way: You can’t recover the input from the hash.
-
Avalanche effect: Tiny changes make the hash look totally different.
-
Collision-resistant: It’s infeasible to find two different inputs with the same hash.

Modern choices include SHA-256 and SHA-512. Older hashes like MD5 and SHA-1 are weak for security, but still useful to catch accidental corruption when copying files. Typical workflow: a project publishes a file and its SHA-256. After downloading, you compute the hash locally. If it matches, the file is very likely intact – like a tracking number that lines up.
What Is a TEE?
A Trusted Execution Environment (TEE) is a secure, isolated area inside a processor. Think of it as a locked safe room inside a building. Sensitive code runs inside; sensitive data is processed inside. Even if the rest of the building (the operating system or cloud admin) is noisy or untrusted, the safe room keeps secrets protected.
Hardware enforces three promises:
-
Data confidentiality: Outsiders cannot read the data while it’s in use.
-
Data integrity: Outsiders cannot change that data while it’s in use.
-
Code integrity: Outsiders cannot alter the code running in the TEE.
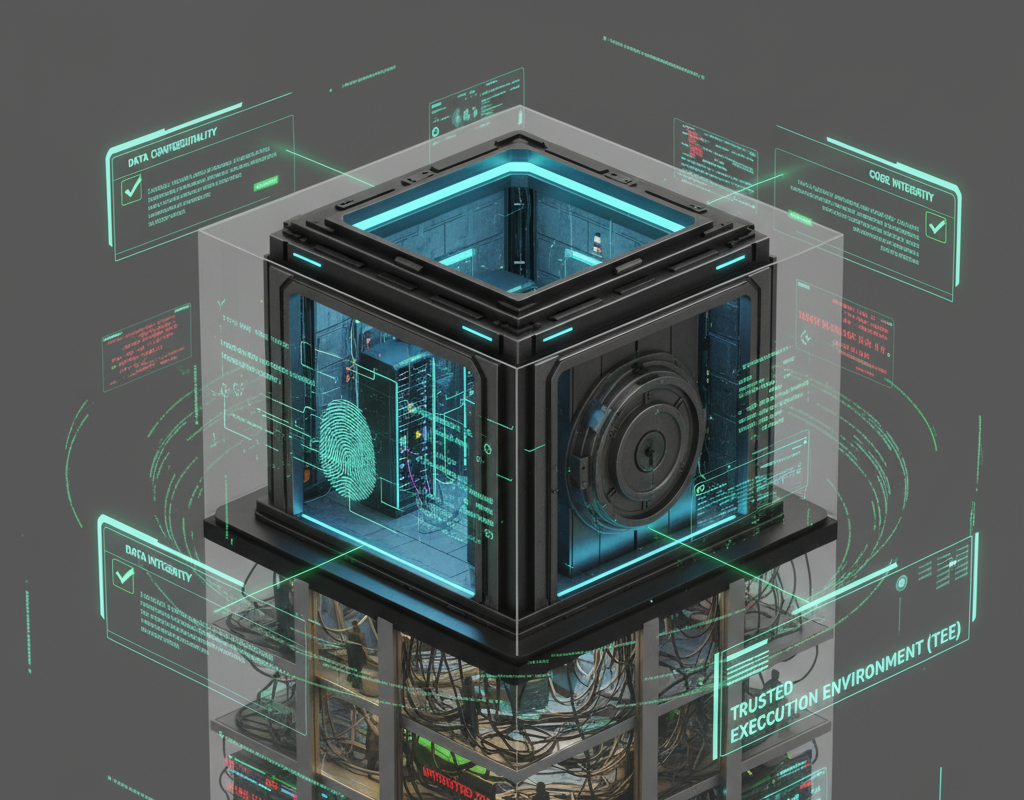
This makes TEEs useful for confidential cloud computing, privacy-preserving AI, and scenarios where you need results from machines you do not own.
Attestation: “Show Your ID Before I Hand Over Secrets”
Everyday metaphor: the verified courier.
The sealed box (integrity) is not enough—you also want to know the courier is genuine. A real courier shows a badge issued by headquarters and may ask you to confirm a one-time pickup code. Only then do you hand over valuable items.
Remote attestation works the same way at a distance:
-
State measurement (the parcel details): The TEE creates a report with measurements—hashes of the app code, configuration, and the TEE’s hardware/firmware versions.
-
Cryptographic signing (the official badge): The TEE signs this report with a hardware-rooted private key fused into the chip—like a badge issued by the manufacturer.
-
Delivery (handing over the ID): The signed report goes to the remote verifier.
-
Verification (call HQ): The verifier checks the signature through a trusted chain back to the chip maker and compares the reported hashes to known-good values. It also includes a nonce (a random challenge) – like today’s unique pickup code—to prevent replays.
-
Secure channel (step inside to talk in private): If all checks pass, the verifier opens an encrypted line directly to the app inside the TEE and can safely send secrets.
Real-world example: Before a hospital uploads patient data to a cloud AI, it verifies – via attestation—that the exact audited model binary is running inside a genuine TEE. Only then does it share the data.
Closing the “Verification Gap”: From Source to Runtime
A sealed box delivered by a verified courier still leaves one question: Who packed the box, and did they use the public recipe? In software, attestation proves which binary is running, not that it was built from the public, audited source code you trust. That’s the verification gap.
End-to-end chain (the recipe, the kitchen, the seal):
-
Source code verification (the public recipe): The source is open for review and audit.
-
Build process integrity (the trustworthy kitchen):
-
Reproducible build: Anyone can follow the recipe and produce the same jar with the same label (identical binary hash).
-
Attested build: If reproducibility is hard, do the cooking inside a monitored kitchen (a TEE) that signs a log binding the recipe version (commit) to the finished jar’s label (binary hash).
-
-
Runtime attestation (the courier + seal): Prove that the verified jar is exactly what’s being delivered and opened now.
With these stages linked, users gain high confidence that “the code we audited is the code that handled our data.”
Bringing It Together
Verification scales from quick file checks with SHA-256 to hardware-backed attestation in TEEs. Hashes are the tracking numbers. TEEs are the safe room. Attestation is the courier showing a badge and a fresh pickup code. And the recipe-to-jar link (reproducible or attested builds) closes the loop between open source and running software. Together, these layers turn “hope it’s fine” into “we can prove it.”
Takeaway
Trust should be earned, not assumed. Start with hashes for file integrity. Use TEEs to protect code and data in use. Require remote attestation before sharing secrets with the cloud. And insist on a verifiable link from source → build → runtime to close the gap.
Reflective Questions
-
Where could simple hash checks prevent mistakes or attacks in your current workflows?
-
Which tasks in your team would benefit most from running inside a TEE?
-
Can you link your source code to deployed binaries (reproducible or attested builds)?
-
What “known-good” reference values and policies will you use to validate attestation reports?
please login with NEAR
Updated: October 10, 2025




Top comment
Verification has another level on web3, but it needs to be improved to complete a 100% verification of products, users and dApps.
🧑 100% userAgree, all this process bring security to all the users
🧑 100% user