We humans have always needed to answer three simple questions: Who said this? Where did it come from? Can I trust it?
Over time, our tools for answering these questions – authentication, provenance, and verification – have changed with technology. This article walks you from ancient clay seals to modern blockchains, showing how each era solved the same problems in new ways. We finish with a practical look at NEAR Protocol, which brings these ideas together on a public, tamper-evident ledger.
Ancient World: Trust You Can Touch
In early societies, people proved identity with objects you could see and feel. Rulers pressed signet rings into hot wax on letters. If the wax seal was unbroken and the
symbol matched the ruler’s mark, readers believed the message was genuine. Armies used watchwords – spoken passwords at the gate—to check who belonged in camp.
Provenance (origin) also lived in marks. Potters, stonecutters, and merchants scratched or stamped goods so buyers knew the maker and place. Coins carried royal symbols to certify value and authenticity.
In that world, an intact seal or familiar mark acted as the verification step – the equivalent of a simple audit. Physical tampering was obvious, and reputation did the rest.
Industrial Era: Papers, Stamps, and Serial Numbers
As trade expanded, we needed consistent rules. Passports and identity papers (standardized after WWI) let border agents check a traveler’s identity with a quick glance and a stamp.
Brands and trademarks helped buyers avoid fakes. “Made in…” labels and factory serial numbers showed where and when a product was made, and which batch it came from – vital for recalls and quality control.
Money and documents added visible anti-forgery features. Banknotes gained watermarks and intricate engravings. Notarized documents and embossed seals became routine to confirm signatures and dates.
Electronics Age: Secrets and Scanners
With computers came new ways to prove “it’s me.” The password (1960s) and PIN for cards allowed machines to check “something you know.” This moved authentication from paper to digital systems.
For provenance, barcodes – and later QR codes – put a scannable ID on each item. A quick scan pulled up the product’s record in a database. This transformed retail, shipping, and inventory by making every item traceable.
Verification became machine-readable. Magnetic stripes, holograms, and later passport chips allowed devices to check authenticity and detect tampering, not just human eyes.
The Web Era: Online Identity and Encrypted Locks
The internet brought usernames and passwords everywhere, then two-factor authentication (2FA) – extra codes or app prompts – to strengthen logins.
Digital content gained signatures too. Software publishers sign their files so computers can verify the source. Social networks began adding “verified” badges for notable accounts, signaling that an authority had checked identity.
On the web, the little browser padlock (HTTPS) means a trusted certificate authority has verified the site’s identity, and your connection is encrypted. Jargon check: encryption is a way to scramble data so only the intended party can read it.
Web3: Shared Ledgers of Truth
Blockchain adds a public, tamper-evident ledger – a record that many independent computers (nodes) agree on. No single company controls the “truth.” Instead, the network reaches consensus (agreement) on what happened and when.
-
Authentication: You prove you control a wallet by creating a cryptographic signature (a secure math proof) with your private key. No central login is needed.
-
Provenance: Steps in a supply chain can be recorded on-chain. Digital art uses NFTs to publish who minted what and when.
-
Verification: Anyone can re-check the ledger later. Timestamps, issuers, and content hashes (fingerprints of files) are open and auditable.
Think of a blockchain like a community bulletin board with locked entries: once posted, entries are time-stamped, linked, and practically impossible to alter without everyone noticing.
How NEAR Protocol Makes It Practical
NEAR focuses on making these ideas usable in daily life and business.
Human-Readable Smart Accounts
On NEAR, an account such as alice.near is more than a username. It can hold code (a smart contract) and keys. A smart contract is a program that runs on the blockchain and follows rules you write. Even subaccounts (like ops.brand.near) can run their own rules and sign actions on-chain. This keeps identities readable for humans while remaining programmable.
Granular Keys for Safety
NEAR supports two key types:
-
Full-Access keys: like owner keys; can do anything.
-
Function-Call keys: limited keys; can only call specific methods with set limits.
This design supports least privilege by default. You can rotate keys easily, keep sensitive keys on a hardware wallet, and give narrow permissions to apps, bots, or teammates without risking the crown jewels.
Analogy: Think of Full-Access as the master key to a building and Function-Call as a key that only opens the mailroom between 9–5.
Subaccounts: Built-In Namespaces for Trust
Any account can create subaccounts under itself – e.g., store.brand.near, nft.brand.near, proofs.brand.near. Only the parent can create names beneath it. This forms a public chain of trust: if it sits under brand.near, it’s endorsed by the brand.
Practical patterns:
-
Keep company.near cold (hardware-secured). Use ops.company.near for daily work.
-
Mint official items from nft.brand.near so buyers can instantly verify they’re under the real brand.
-
Issue credentials from diplomas.university.near and check them by namespace and signature.
Smart Subaccounts: Policy at the Edge
Because every (sub)account can run code, you can encode rules like multi-approval, spend limits, time locks, and role-specific keys. You can even automate actions (e.g., auto-mint a receipt when a delivery status changes to “delivered”). This spreads risk: the root account stays offline while working subaccounts operate with tight permissions.
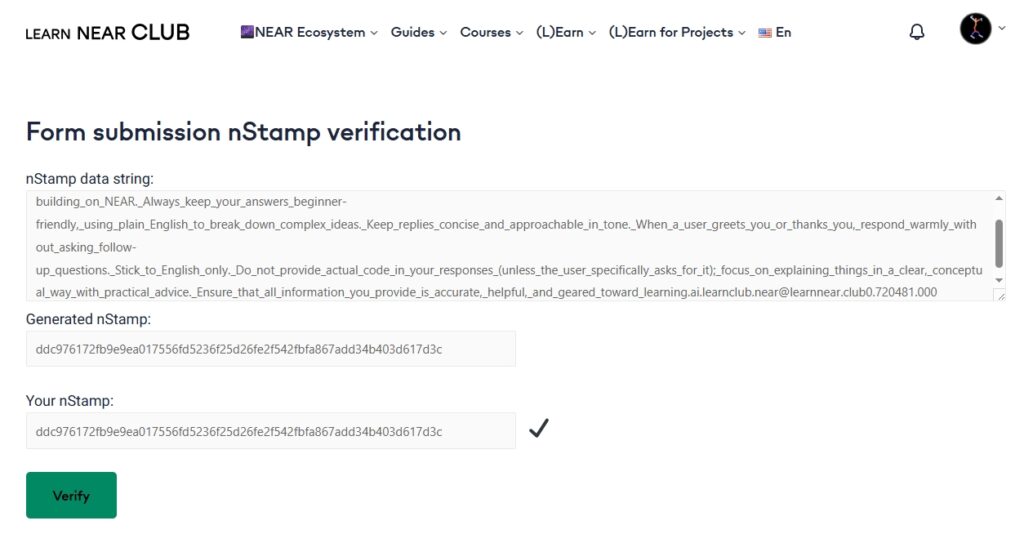
nStamp : One-Click Provenance
: One-Click Provenance
nStamp lets you take any digital artifact – file, form, image, or AI output – create a hash (a unique fingerprint), and write the fingerprint plus timestamp to NEAR from a known account (e.g., proofs.brand.near). Later, anyone can re-hash the original and instantly check issuer, time, and integrity without revealing the content. This is ideal for receipts, certificates, original content, and verifiable AI answers.
Why This Matters
-
Authentication: Sign in by proving control of you.near. Delegate safe keys to subaccounts for teams and automations.
-
Provenance: Publish and mint from *.brand.near. Your public namespace and on-chain history expose fakes fast.
-
Verification: Use nStamp to create immutable timestamps and fingerprints that anyone can check in seconds.
Takeaway
The journey is continuous: from wax seals to passports, from barcodes to HTTPS – and now to shared ledgers. Blockchains keep a public, auditable record. NEAR makes that record usable: readable names, smart (sub)accounts, fine-grained keys, and nStamp for instant proofs. The tools are ready today to help you answer those timeless questions with less doubt and more confidence.
Reflective Questions
-
Where in your work or life would subaccounts (like ops.brand.near) reduce risk while keeping things simple?
-
Which documents or outputs could benefit from an nStamp fingerprint so others can verify them later?
-
What tasks could you hand to Function-Call keys to avoid sharing full access?
-
If a customer asked, “How do I know this is authentic?”, how would your current process compare to using NEAR?
Updated: December 17, 2025





Top comment
world move fast
🧑 100% userHi
🧑 100% userHuman learned to learn but still learning it's great
🧑 100% usergo ahed
🧑 100% user